by Cian O’sullivan
The trend to develop and deploy cloud native applications; that is applications and software developed to operate in cloud environments; is generally well established and well understood.
Statistics such as “By 2025 Gartner estimates that 95% of new digital resources will be deployed on cloud native platforms”; are hardly surprising to anyone in the industry.
This rapid fundamental shift in how applications are architected, developed, built, deployed and run has generally resulted in the organic adoption of many discrete and point based security solutions to address particular aspects of cloud native application security.
Particularly in larger organisations it is not atypical to see multiple development teams each procuring and operating their own code scanning tools. Certain discrete security tools that perform source code scanning; some performing software composition analysis on certain 3rd party packages and libraries; another solution performing secret scanning or infrastructure as code scanning.
And that is just in the development lifecycle; the adoption of both point based security solutions as well as solutions that have overlapping functionality is often seen in run time environments as well. In the case of cloud security posture visibility and assurance – It is quite common to see organisations using a native Cloud Security Posture Management (CSPM) tool and, in addition, a third party CSPM that has similar key features to the cloud native one in many respects.
With cloud workload protection we encounter examples of platforms providing protection on stateless or ephemeral assets like containers whilst another platform performing a similar function on traditional stateful virtual machine workloads.
There are often many opportunities to rationalise and consolidate solutions and toolsets.
This adoption of multiple tools generally tends to be an organic by-product of the rapid acceleration of cloud native application security requirements in recent years.
The problem space is clearly evident:
- Proliferation of point security solutions
- Minimal context of alerts or identification of qualified risks between solutions
- Significant operational overhead for team to manage multiple tools
- Duplication of capabilities across multiple tools
- Inconsistent approach
- Extensive licence costs
- Ambiguity around ownership, prioritisation of issues and actionable insight
The ultimate impact of course is the ability for organisations to appropriately identify and remediate risk is fragmented and subsequently limited and ineffective.
Cloud Native Security Security Platforms
Cloud Native Application Security Platforms (CNAPP) offer an integrated set of security capabilities across development and runtime environments. They present an opportunity to consolidate previously siloed security capabilities including code and artefact scanning, entitlements management, contextual cloud posture management and cloud workload protection capability.
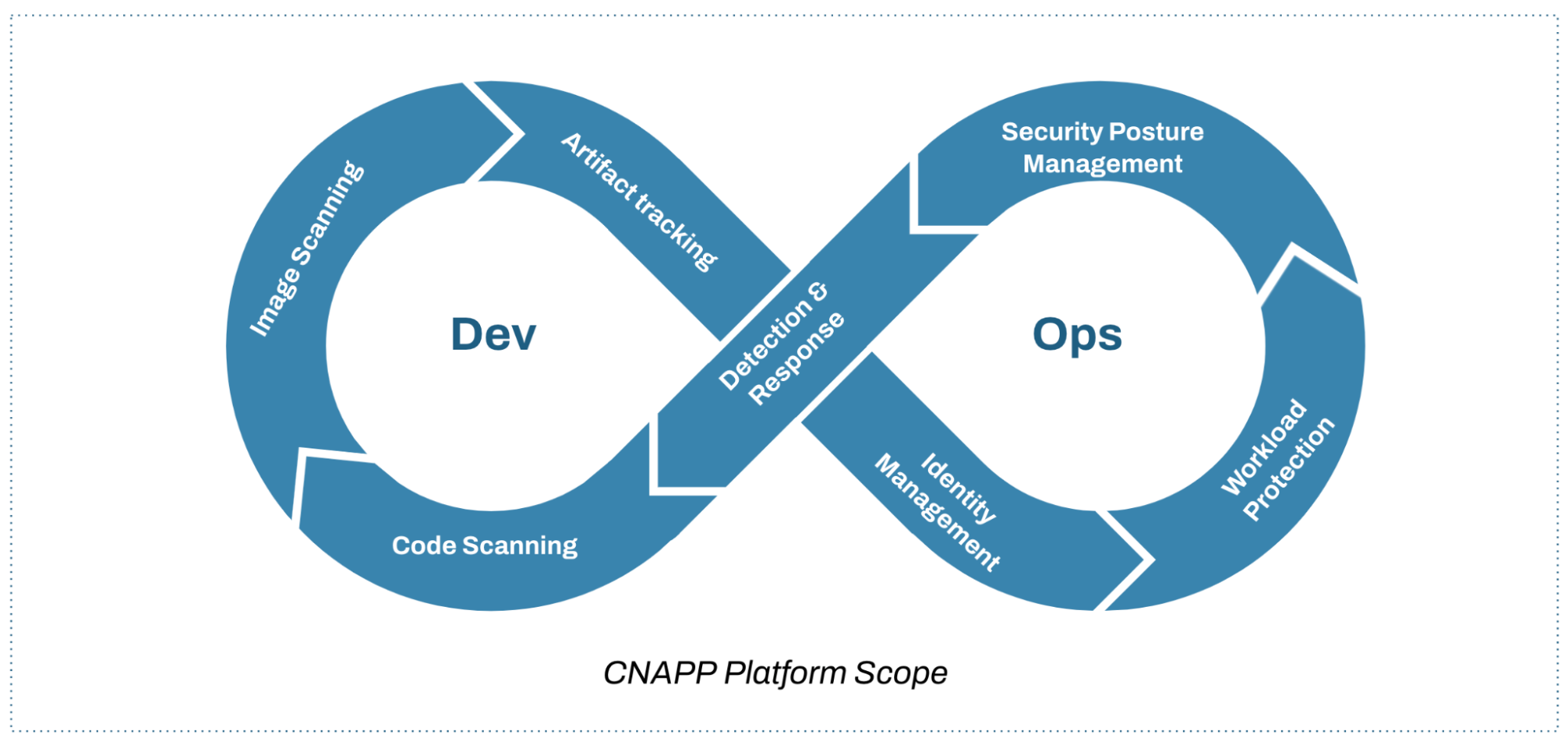 By integrating vulnerabilities, misconfigurations, and relationships across the development life cycle, and by providing context of the assets, users and environments in run time environments; excessive risk can be surfaced, subsequently enabling development teams and product owners to focus on remediating the areas of the application that represent the most risk.
By integrating vulnerabilities, misconfigurations, and relationships across the development life cycle, and by providing context of the assets, users and environments in run time environments; excessive risk can be surfaced, subsequently enabling development teams and product owners to focus on remediating the areas of the application that represent the most risk.
Evaluation Considerations
Selecting the right CNAPP platform is an important and key part of a cloud native security strategy to support and secure your organisations digital transformation. Having a robust evaluation methodology is important to selecting the most suitable CNAPP platform to support this strategy.
A key part of the methodology is defining and scoring against evaluation aspects or categories. However the intent here is not to go into specific detail on the methodology nor the full list of evaluation dimensions rather list some of the sample core functionality evaluation aspects for consideration.
Cloud Platform Coverage and Capability
In many cases; coverage would be classed as one of the mandatory criteria used to refine a market list of CNAPP candidates down to a shortlist. Many enterprises will have a multi-cloud strategy and therefore will require a CNAPP platform that supports multiple cloud providers.
The level of depth of coverage and capability across each cloud provider will vary across CNAPP vendors so candidates’ maturity on each platform against this criteria. If, for example; AWS and GCP are a key part of your organisational cloud strategy, then look at CNAPP platforms that can provide 100% coverage across varied workloads such as serverless, containers and VMs within both clouds.
Look at refining your market scan to a shortlist of CNAPP providers that provide contextual risk visibility across both the control and workload plane by combining metadata from the cloud provider API and the storage layer. The more context that is provided by a CNAPP platform on a potential risk; the higher value that information is to the teams that ultimately have to triage and either resolve or acknowledge the risk finding. Platform teams and security operations teams are already weary from alert fatigue so a CNAPP platform that can provide high value context will ultimately save you time, effort and reduce your MTTR in the future.
Data Security Posture Management
Data is generally one of; if not the most important assets for organisations and maintaining its confidentiality and integrity is one of the leading challenges for security teams today.
Lack of data classification, misconfigurations around access controls for sensitive data, challenges managing regulated data and associated compliance and an inability to detect and prevent production data entering non production environments are all common issues faced today within cloud environments (I would add quickly; of course similar challenges are faced with data within on premise environments but given this is a discussion on cloud native security we have to focus on data in cloud environments).
Some of the leading CNAPP solutions are now starting to introduce capability to identify, prioritise and address data-related security risks in cloud data stores making this a very useful and beneficial evaluation criteria for many organisations. As an example we have observed a CNAPP platform we have used was able to validate the validity of credit card data detected within a cloud data store providing very valuable insight for the client. Be aware there will likely be some shortcomings in terms of false positive alerts detecting data types whilst the capability develops and matures. Performing a Proof of Value of one or two shortlisted CNAPP platforms will provide you further insight into current capability and use cases.
CI/CD Security
The development of this criteria will depend on your existing processes and toolsets in your development lifecycle. In a general sense you will be looking for a CNAPP platform to build security into the CI/CD process whilst not introducing unnecessary friction on your developers. Your organisation may already have a mix of open source and commercial security tools performing various types of scanning functions in the development lifecycle and consolidation and reduction of tools and complexity may be a key requirement whilst maintaining functionality. Uncovering these details will form various criteria within this category.
Integrations
Integrations can feed a number of specific evaluation criteria. Again these will be specific to each organisation depending on the nature of their environment and platforms in use. Consider CNAPP vendors that offer automation capability for third-party platforms that are in use within your environment to support existing and new workflows. Some common questions/examples that can drive specific criteria in this category:
- Does the CNAPP vendor support integrating with existing IT service management platforms in use?
- For image repositories does the CNAPP solution integrate with the current image repositories in use?
- Does it integrate with existing CI/CD tools in place?
- Does the CNAPP vendor support your organisation’s SIEM platform?
Technology Evaluation Methodology
A thorough evaluation is highly recommended to ensure the appropriate organisational context is uncovered, relevant stakeholders are consulted, requirements are collated and distilled into appropriate evaluation criteria covering both functional and non functional domains; which are then scored against in order to select the most suitable platform for your organisation.
Mantel Group has an established methodology and proven approach to performing evaluations such as CNAPP technology for clients. Our process is objective, transparent and robust and delivers an outcome that provides clients confidence with proceeding with what can be a significant strategic security investment.
If you are looking for specialist support in building and implementing a security strategy please reach out to our team at Mantel Group.