Key Results
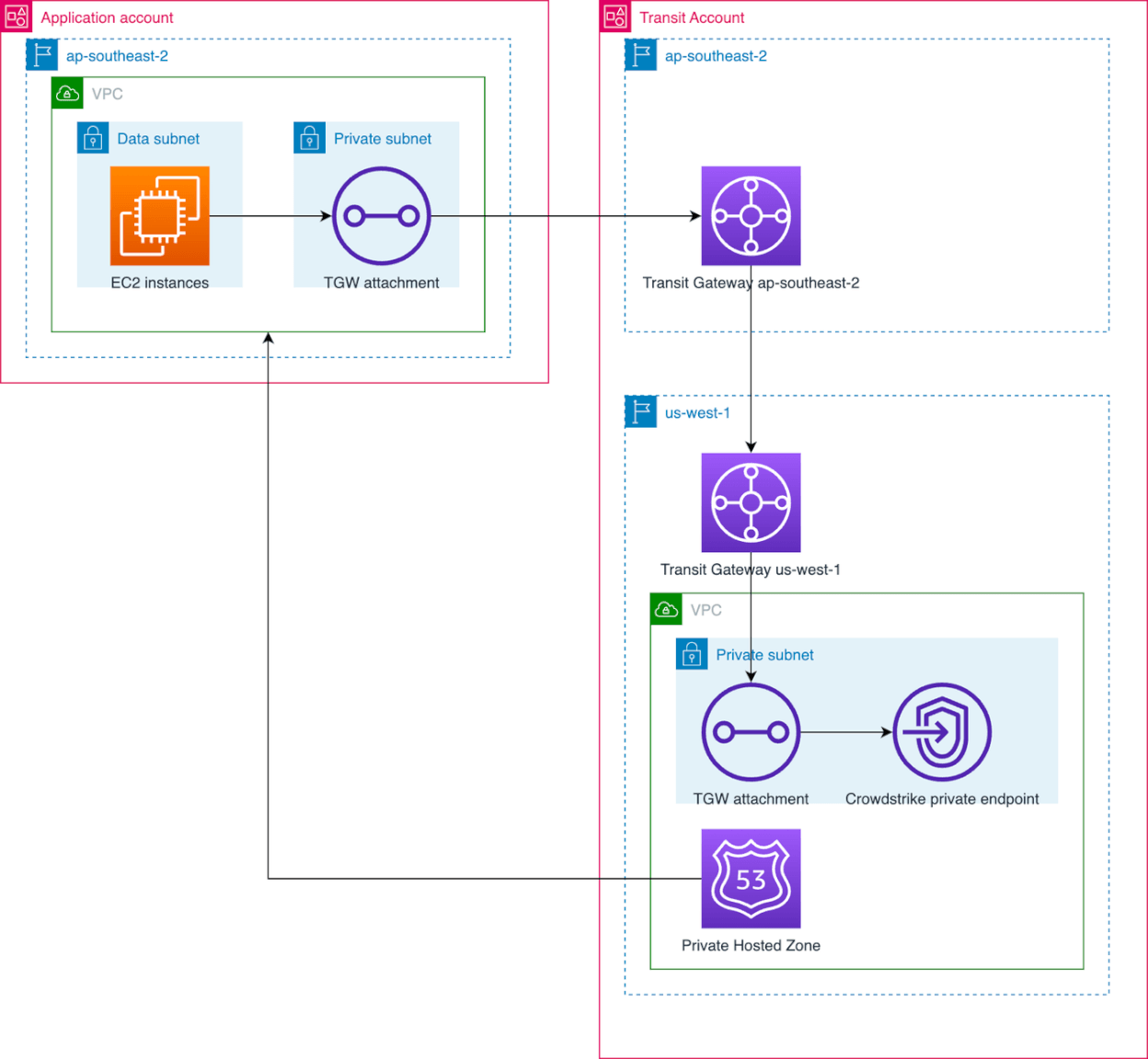
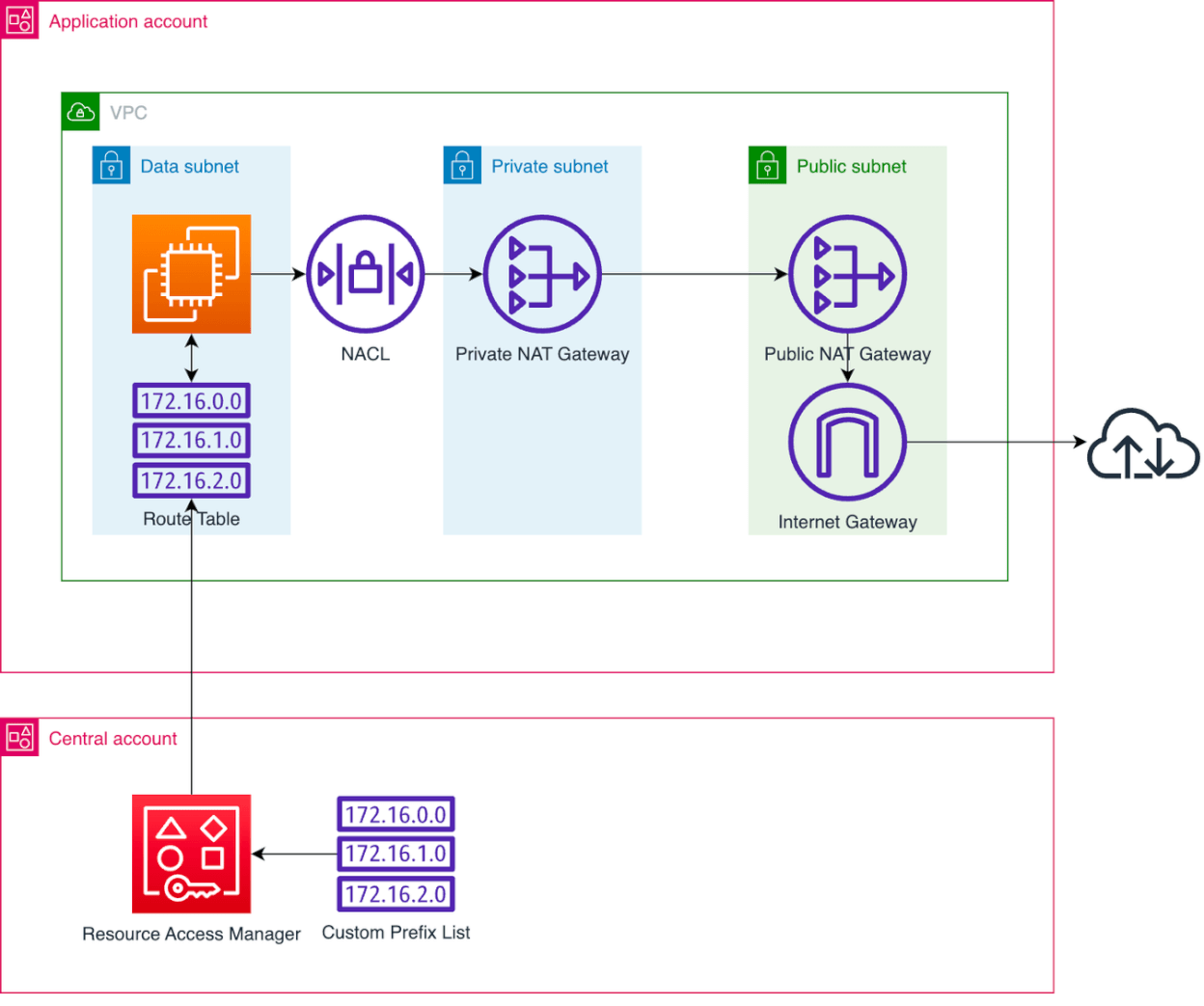
The customer`s AWS workload became a more secure environment where access from the data tier to the public internet is restricted to the minimum possible IPs while all other traffic goes through VPC endpoints. In addition, all data is encrypted both at rest and in transit with mutual TLS in place for any application access. This means that this particular environment is more secure, but as everything was built to be reusable, these benefits were subsequently shared with multiple environments with minimal effort.
Key Products/Services we used
- Amazon Virtual Private Cloud (VPC) segregated into network tiers for hosting component services within subnets – Public, Private, and Data.
- AWS Transit Gateway controlling all inter-VPC and cross-region traffic routing.
- NLB for ensuring load balancing among the instances
- Amazon Elastic Compute Cloud (EC2) for the various applications and databases.
- AWS Lambda primarily for event-driven, asynchronous, serverless compute used for triggering events.
- EBS and EFS for file storage.
- AWS Key Management Service (KMS) for customer controlled key management through customer-managed keys.
- Private Certificate Authority for provisioning and managing SSL/TLS certificates that are used for internal communication and mutual TLS.
- AWS CloudTrail, Amazon CloudWatch, Flow logs for monitoring and logging native AWS components and deployed applications.
