command from the terminal. Once the repo is copied down you will find a file called config.sh open it in a text editor and plug in the values you see between the < > symbols.
The values you are interested in are, PROJECT_ID, REGION, ZONE and IAP_USERS. The first three should be straight forward and will depend on what name you have given your project and what region/zone you would like the resources deployed, select a region/zone closest to you. The last value is a little more obscure and I have tried to explain in the comments how to format it. You have a few options here;
To specify a single use just put;
export IAP_USERS=’[“user:bob@example.com”]’
To specify multiple users make it in a list format;
export IAP_USERS=’[“user:bob@example.com”,
“user:john@example.com”]’
To specify and entire domain use this format;
export IAP_USERS=’[“domain:example.com]’
Go into your Google Console and create the project with the same name you have mentioned above. Now simply run deploy.sh from the command line. The script will spin up cloudbuild and deploy the terraform. Once complete the script will output an IP address, make a note of this. This address will be the source address of any connections that are established through the proxy.
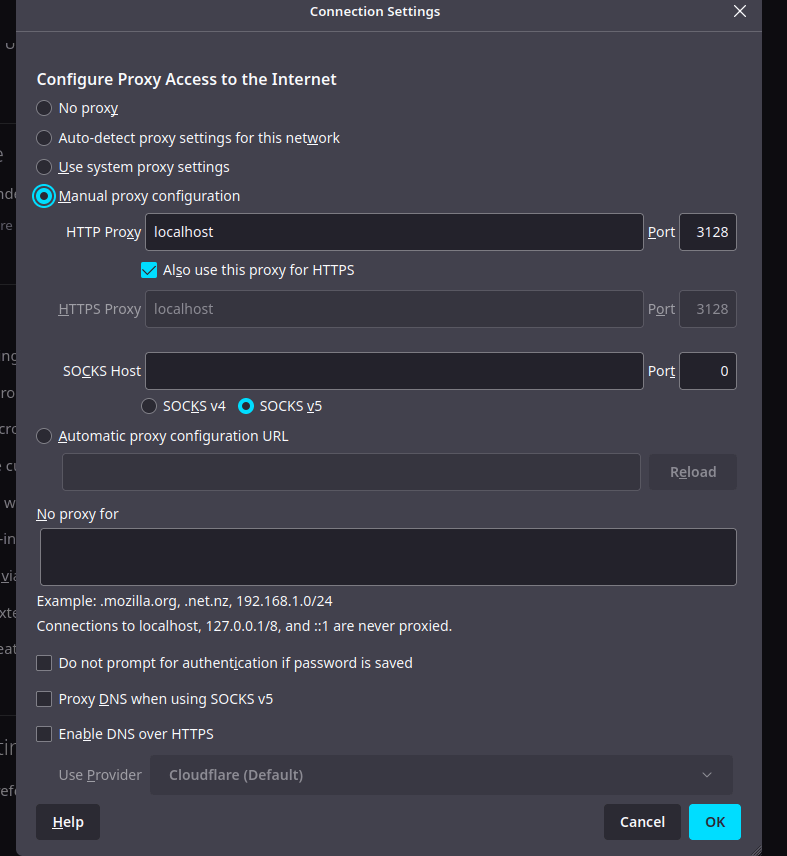
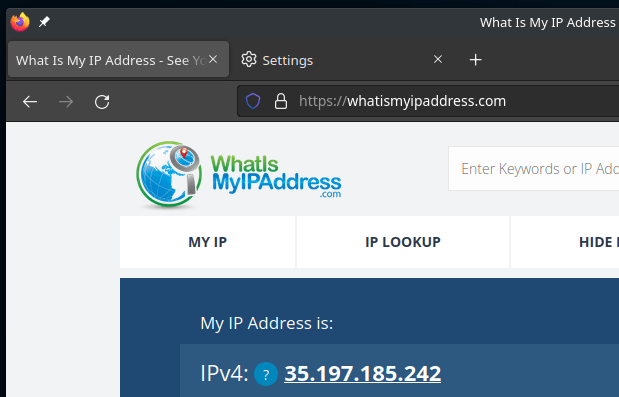
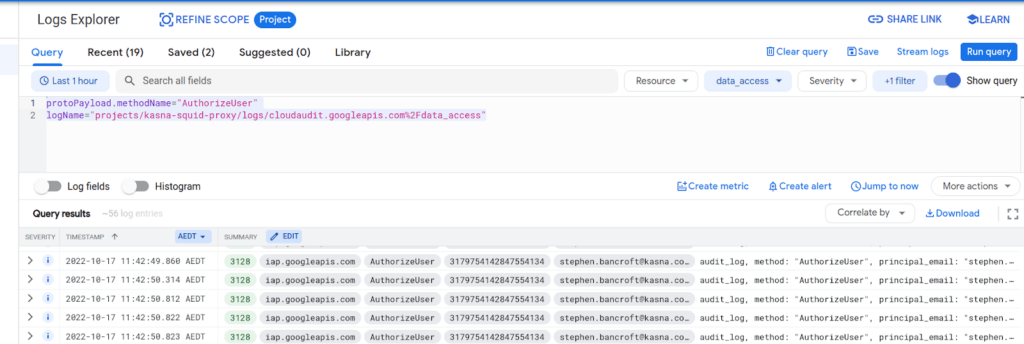
Then you should be able to see who has logged in using IAP;
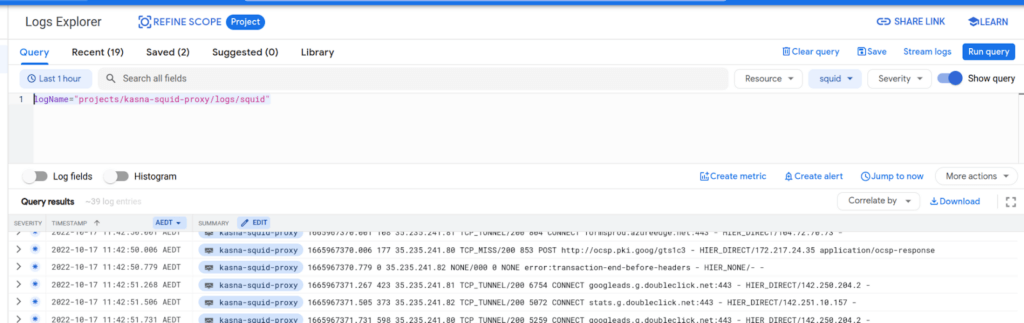
To see the Squid access and error logs, you need to set up a log query to look for;
Then you should see logs as per;