Introduction
Using multi-account strategy is the best practice in AWS, which has been adopted by many organisations. In my observation, a lot of cloud engineers still use Incognito mode to switch between accounts. When there are more than two accounts, they have to constantly sign out and sign in to a different account, which can become a big time waster. I will introduce methods to switch accounts in console and CLI, in personal and corporate environment.
Account switching in Management Console
Personal Environment
Let’s look at account switching in personal environment first. Here, personal environment refers to the setup where you have administrative access.
IAM Identity Center (Successor to Single Sign-On)
In my opinion, this is the best approach so far because we can keep multiple accounts’ windows open. Here’s the guide to set it up in the console.
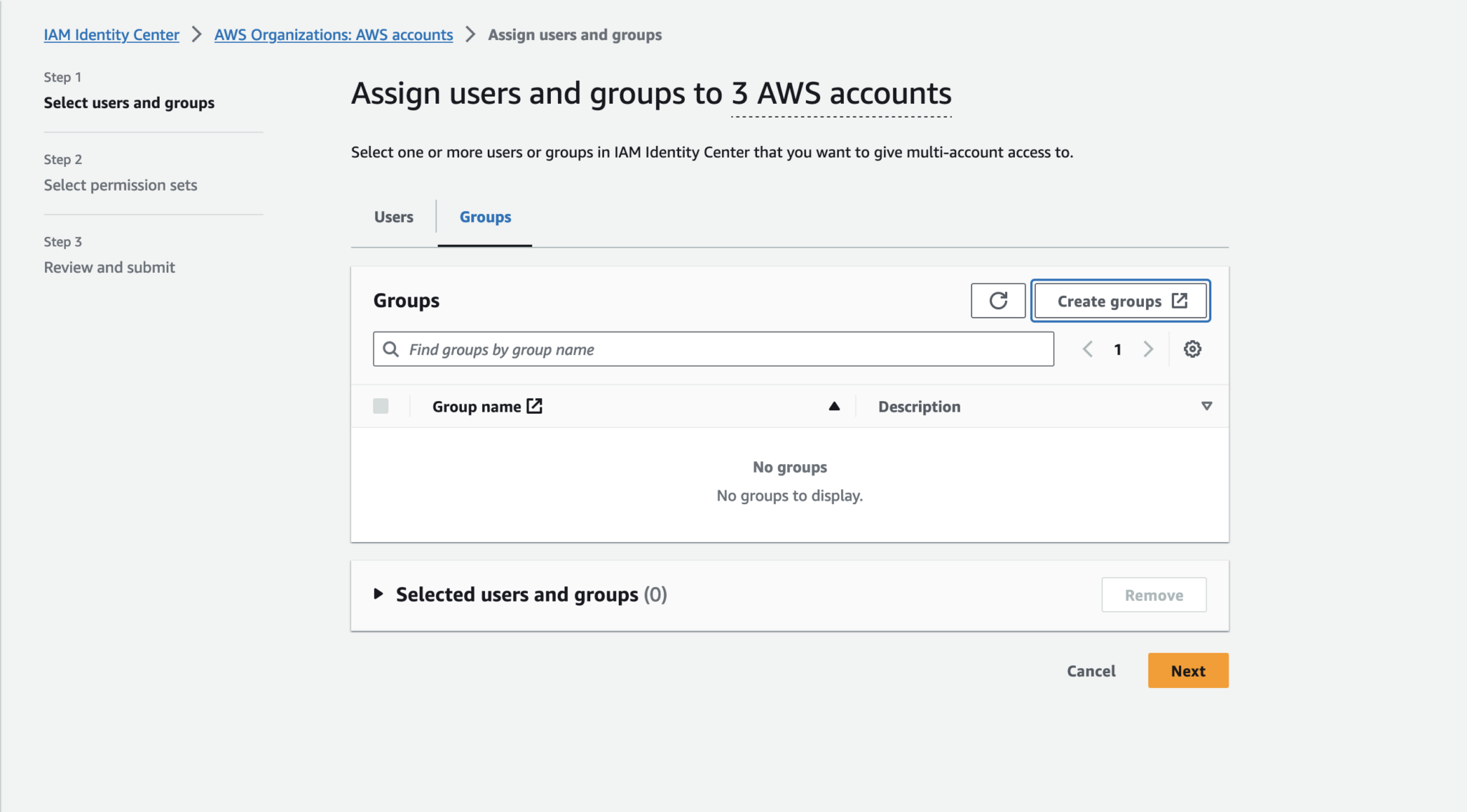
Log into the management account, enable IAM Identity Center, click “AWS accounts“ under Multi-account permissions. Select all accounts that you want to enable SSO, click “Assign users or groups“.
 Identity center entry
Identity center entry
 Create a user
Create a user
The email address we put in this form will be the one to receive the invitation to access AWS portal. We will also get AWS access portal URL.

User

Assign user
Here, since there’s no permission sets listed yet, we need to create it first.
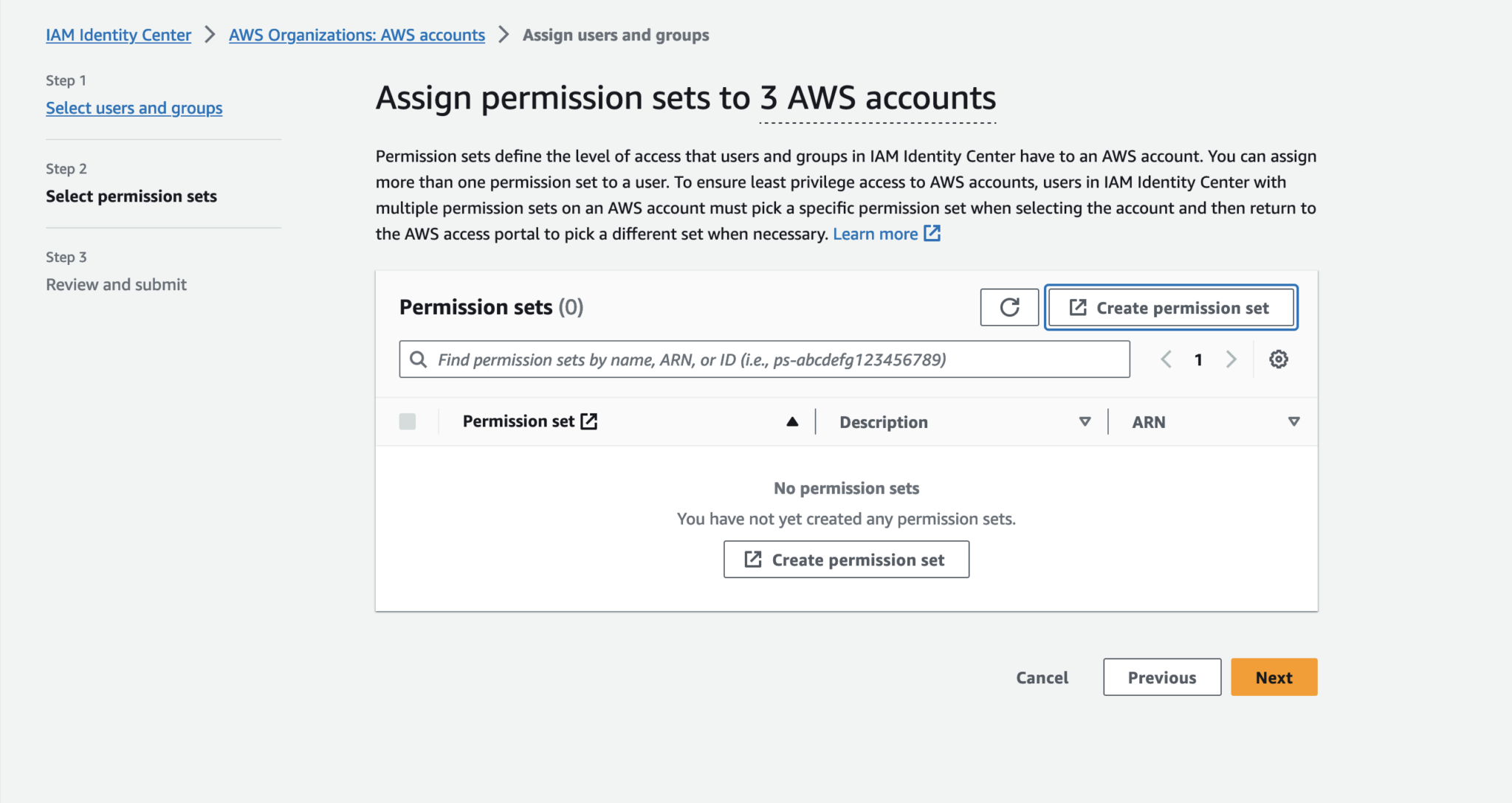
Create permission set
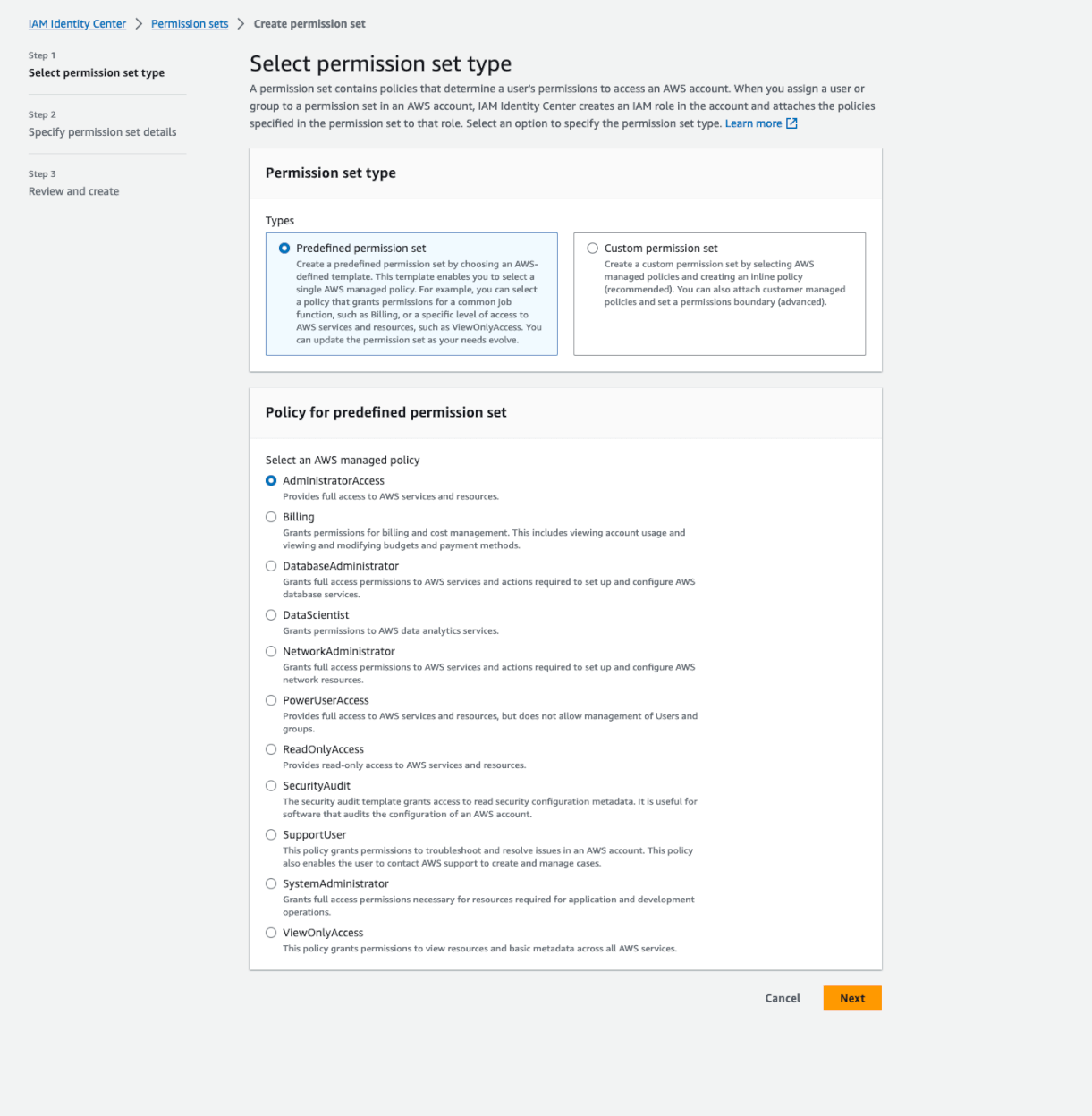
Permission set
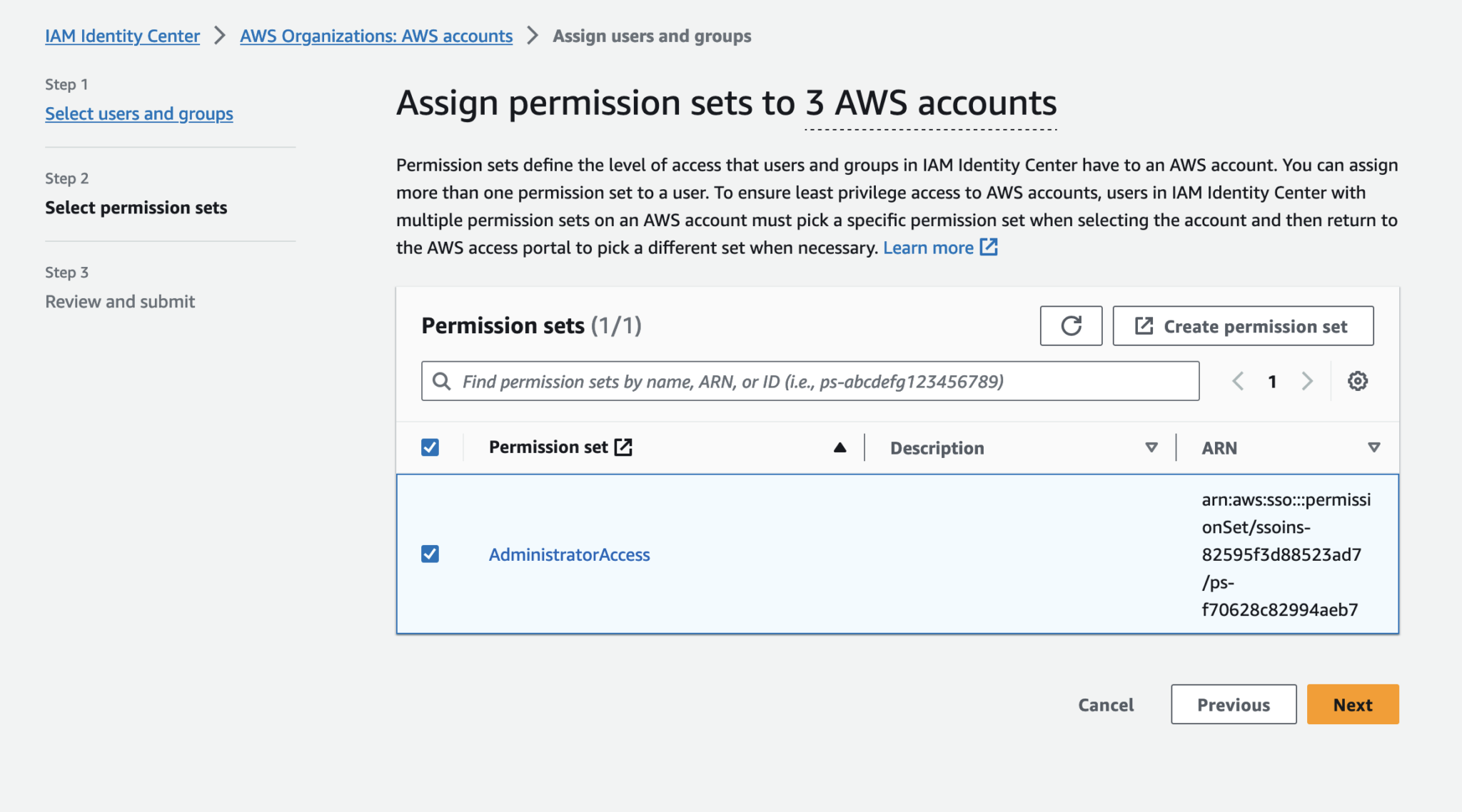
Assign permission set
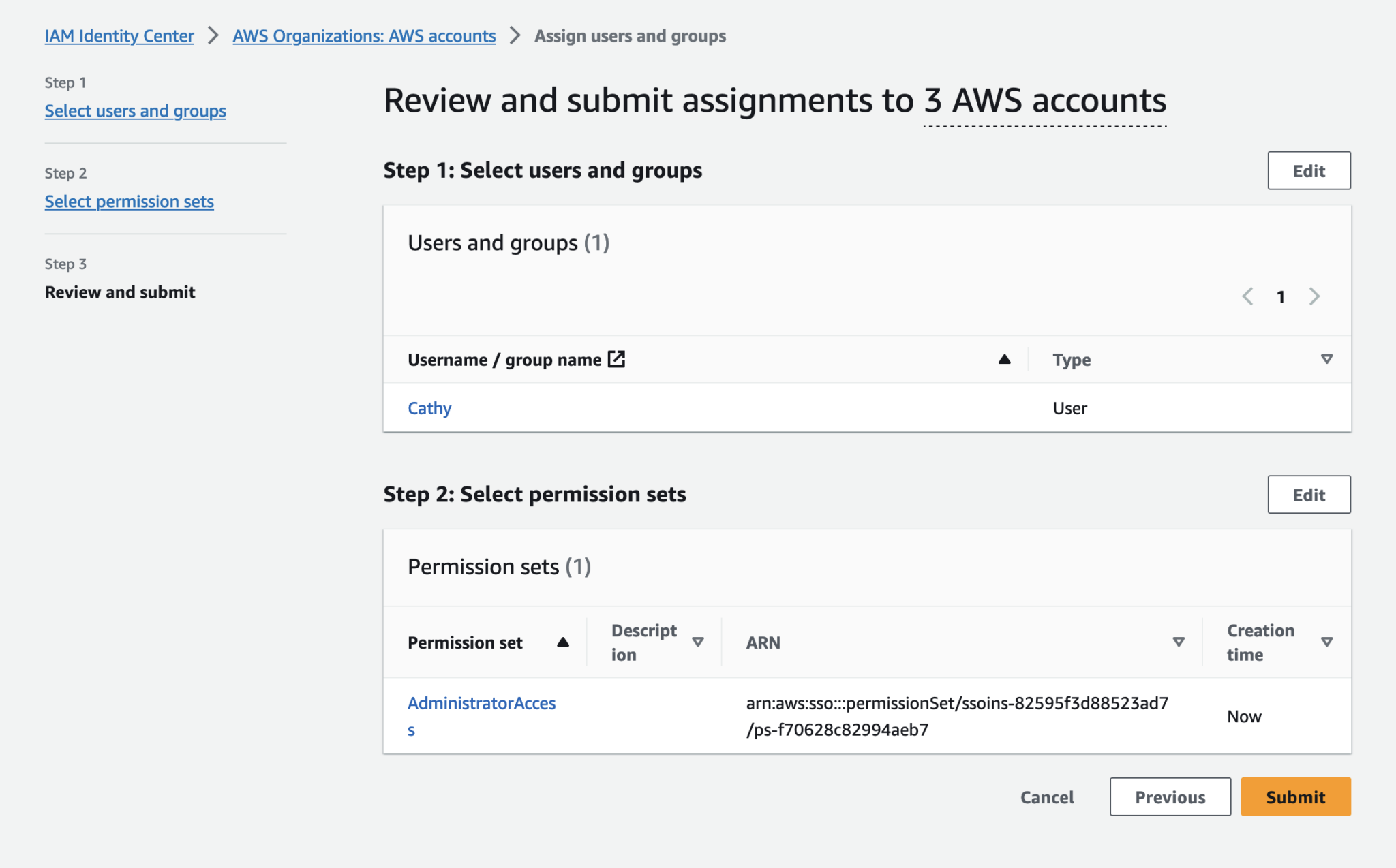
Review and submit
Now let’s find out the email and follow the instruction to create new password, then log in.
TA-DA! Your setup is done! You will see your screen like this!

SSO login page
Switch Role
This is a feature provided by AWS. You can either be in account A or B.
Say, if you’re logged in account A, and want to switch to account B, you need to create a role in account B to allow this. You can set up permissions as you like, but make sure the trust policy is set up like the below.
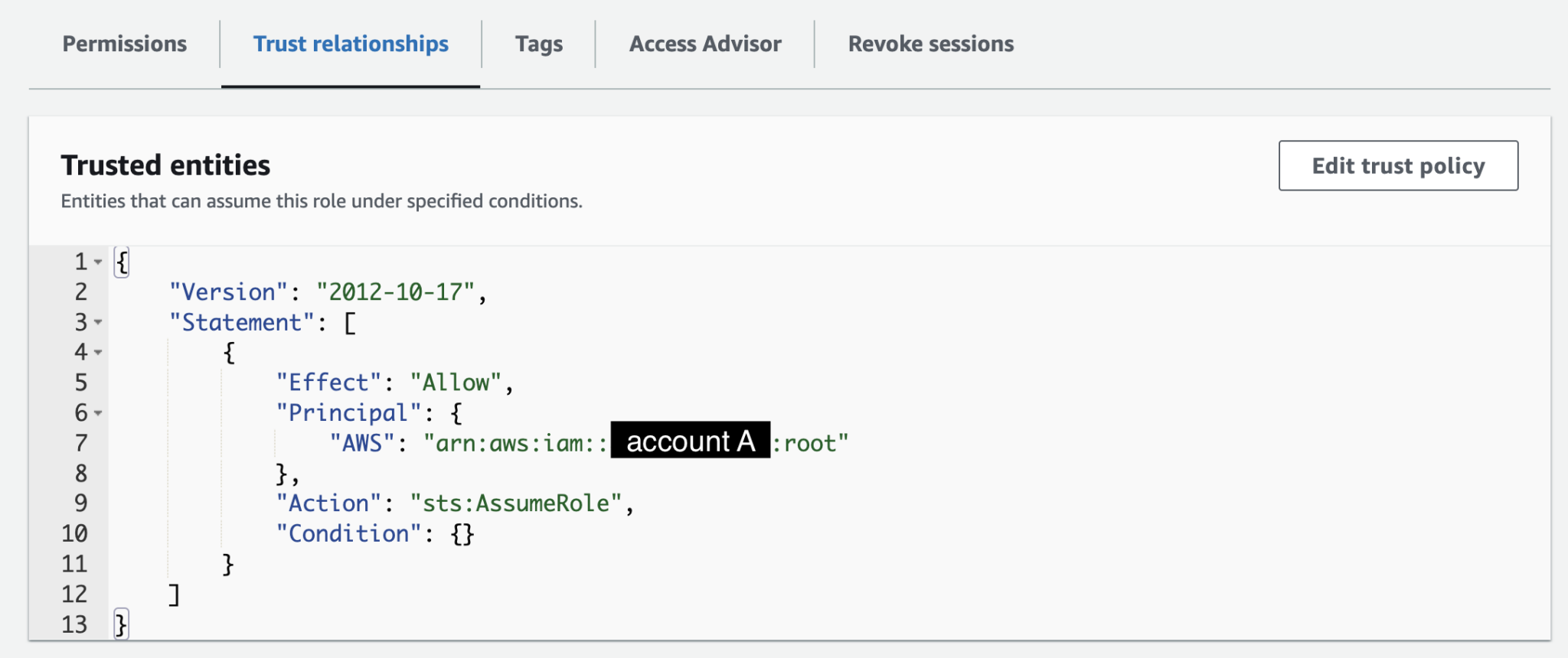
Trust policy
Now we log in as account A, clicking “Switch role“ will take us to the popup window.
The value of Account would be the account B id while the value of Role would be the role you created in account B.
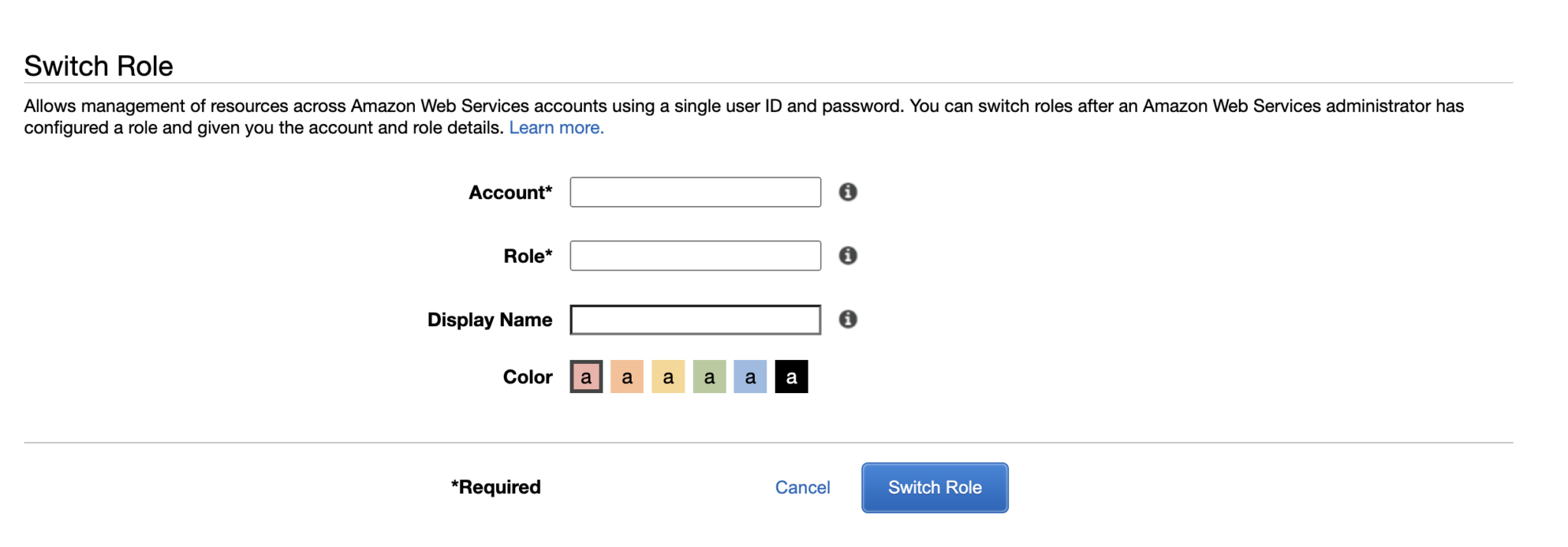
Switch role setup
If you switch successfully, you will see this.

Switch successfully
AWS Extend Switch Roles addon
There are some limitations to using Switch Role. Most importantly, the history can only show a maximum of five records. Every time you want to switch to the account not shown in the history, you have to enter the account and role again. If you use Firefox, I would suggest using AWS Extend Switch Roles extension.
Click “AWS Extend Switch Roles“ in the Extensions list.
Extension
You will see an error message at the first time you open this extension. Ignore that and click “Configuration“.
Error
Follow the example shown at right hand side to fill in accounts that you want to switch to.

Configuration
When it’s all configured, when next time you open this extension, you can see the role list.
Role list
Corporate environment
If your organisation uses IAM Identity Center, you’re quite lucky! You don’t need to set up anything to SSO.
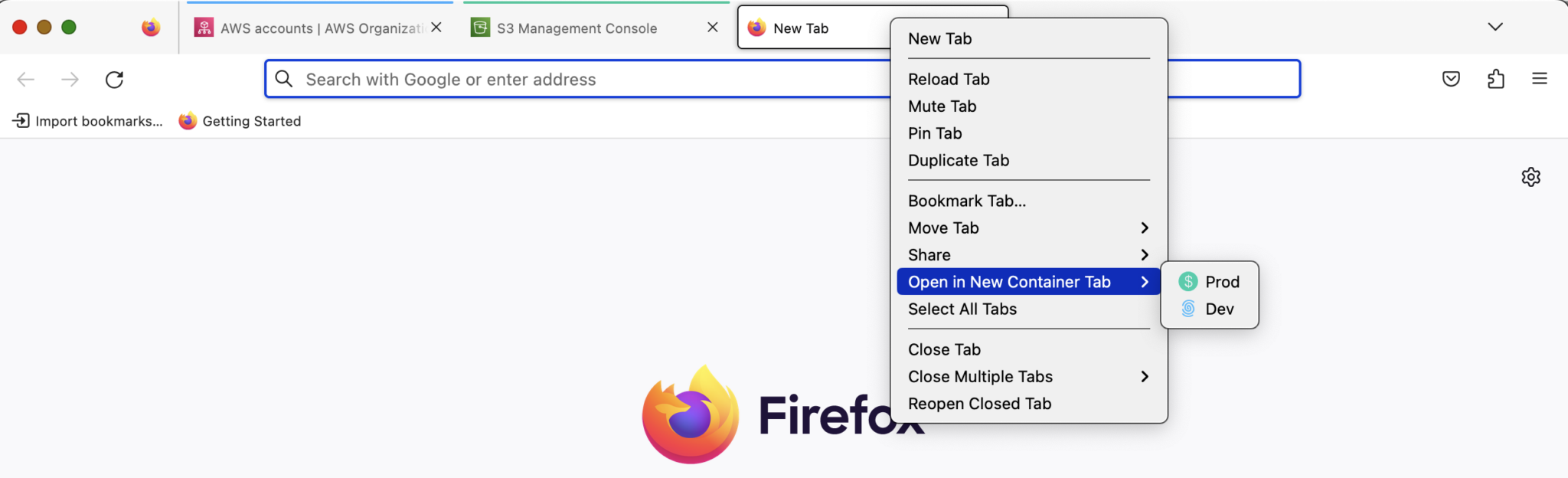
In most cases, you can’t assume a role in an account and don’t have permission to create those roles. I would recommend using Firefox Multi-Account Containers – Get this Extension for 🦊 Firefox (en-US). Interestingly, this extension is not built for AWS account switching.
The container setup is quite simple.
Extension
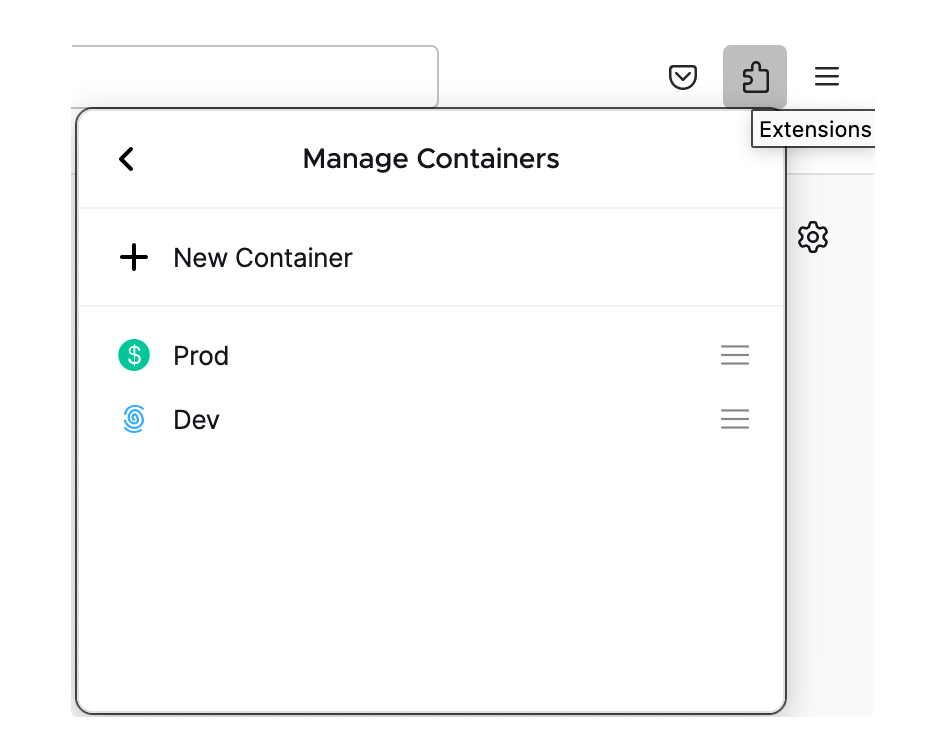 Add containers
Add containers
Cool! Now you can see “Open in New Container Tab“ option when you right-click a tab page.
Open a tab in selected container
Open a tab in a selected container
Account switching in CLI
The prerequisite to use CLI to interact with AWS is that you have programmatic access. Switching account in CLI is very simple. It is through –profile. For example,
aws s3 ls --profile PROFILE_NAME
You can also setting profile name for all without setting it again in each call.
export AWS_PROFILE=PROFILE_NAME
Configure profile in CLI
% aws configure --profile PROFILE_NAME
It would prompt you to fill in the following 4 variables.
AWS Access Key ID [None]: AWS Secret Access Key [None]: Default region name [None]: Default output format [None]:
It’s not mandatory to provide all values now. You can leave some blank.
Configure profile in file
As you may have noticed already, a profile setup contains 2 parts, credentials and config. AWS has files to store the data. So we can directly edit credentials and config files under ~/.aws folder. They look like these:
[default] aws_access_key_id = xxxxxxxxxx aws_secret_access_key = xxxxxxxxxx [dev] aws_access_key_id = xxxxxxxxxx aws_secret_access_key = xxxxxxxxxx [prod] aws_access_key_id = xxxxxxxxxx aws_secret_access_key = xxxxxxxxxx
[default] region = us-east-1 output = txt [profile dev] region = ap-southeast-2 output = json [profile prod]
If you name your profile default, that profile would become the DEFAULT one when no –profile parameter is provided.
Summary
Without you realising, account switching is one of the things that we do a lot in day-to-day work. However, I have seen too many people wasting time in this. If you have admin permission and want to log into console, you have many options. Personally, I would choose IAM Identity Center over Extend Switch Roles addon. Plain Switch Role feature would be my last choice. If the above three methods don’t work or you’re in a corporate environment, you can utilise browser container extension. Switching account in CLI is fairly simple. All you need is programmatic access and saved files of credentials. Well in the end, I hope that you enjoyed this article or have learnt something new.