In today’s fast-paced digital world, cyber threats are on the rise exponentially and are a constant stress point for organisations. Remediating any security incidents require logs from different resources and entities involved and traditional approaches to security data log ingestion, normalisation and retention can become expensive with little traceability to business value and risk reduction. Additionally, the security teams spend more time in collating and finding the right relevant events for investigation and resolving attacks. Often organisations reduce the retention periods due to high storage and ingestion costs which reduces the effectiveness of machine learning and impacts forensic capabilities and non-compliance to specific regulations and standards.
To stay ahead of the adversaries and have proactive mitigation in place for potential threats and protect their assets and sensitive information, cost effectively centralising, normalising and retaining security logs has become essential for organizations across the globe. This allows organizations to have an accurate and unified view of their environment and the related security events, increasing their ability to respond effectively to potential security incidents, use machine learning for rapid detection and event correlation and supporting forensic analysis. With valuable security insights from the centralized security data sourced from various systems and applications, security teams can easily detect and respond to potential security threats before they escalate.
While different security organisations and vendors present security data in different formats, it becomes cumbersome to correlate the data and do in-depth analysis. This challenge is solved by leveraging the Open Cybersecurity Schema Framework (OCSF) schema which is a standard schema for security events across the board Adopting OCSF, different vendors and organisations can ingest and analyse security data across different platforms. By consolidating security data at one location in a standard format, security teams can investigate security incidents more quickly and effectively. thereby respond with greater agility. This is critical in today’s ever-changing threat landscape, where the ability to detect and respond quickly to security incidents is paramount.
For example, with all the relevant data in standard format, customers can use machine learning models to identify anomalous behaviour in their network traffic or to predict when a security incident is likely to occur. They can also use correlation rules to detect suspicious activity across multiple data sources and to prioritise security alerts based on their level of severity.
Centralising security logs also offers significant benefits in terms of compliance with industry-specific regulations. Centralising security logs provides a location for auditing and reporting on security events, enabling organisations to meet compliance requirements efficiently.
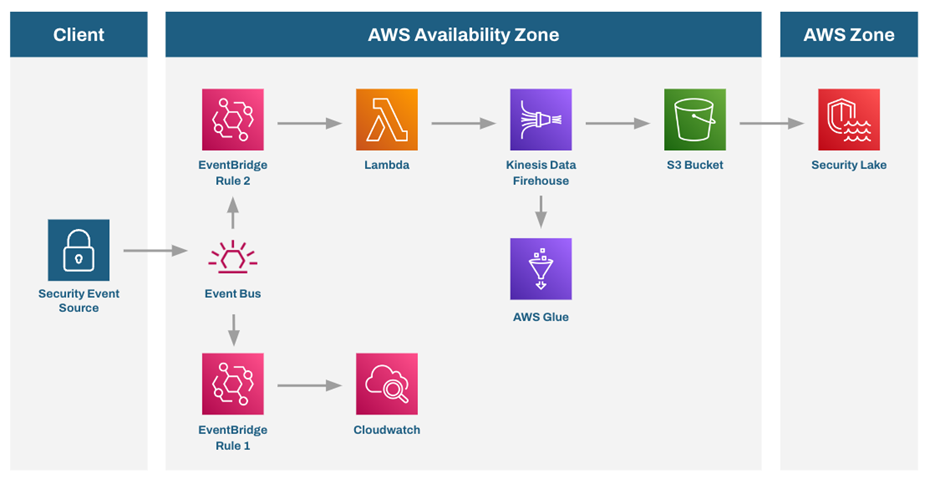
With Amazon Security Lake, Mantel Group can help organisations centralize their security data from cloud and on-premises sources in their own AWS account, implement cost effective advanced analytics, machine learning and threat detection/correlation to gain insights into their security data while being confident that all relevant and right data is being ingested and retained for the appropriate amount of time.
Mantel Group Security Data Lake Accelerator
The Mantel Group Security Data Lake accelerator can help organisations maximise their return on investment and expedite time to value by streamlining security data lake design, implementation, integration and optimisation using a proven approach and infrastructure as code libraries with patterned integrations to leading solution providers. Mantel Group can accelerate the operational management of an Amazon Security Lake solution including integration with 3rd party security event data sources from EDR providers such as Crowdstrike and Identity and Access Management providers such as Okta, Azure Active Directory, Sailpoint and others.
For organisations who wish to use Security Lake as the foundation of a managed detection and response capability, Mantel Group offers a fully managed security detection and response service to respond to alerts generated by curated Security Lake detection rules that are continually updated based on the latest threat intelligence. Powered by Cloudtrace, this service is delivered using a 24×7 security operations centre staffed with experienced blue and red teams.
By leveraging AWS Security Data Lake, our customers can enhance their security visibility through cost-effective collection, collation, and storage of logs from multiple sources. At Mantel Group, we have experienced this firsthand, as the solution has enabled us to capture and store logs from various enterprise systems (such as Okta, AWS and Crowdstrike) at a fraction of the cost of traditional SIEM solutions. With the ability to perform advanced analytics and reporting on our security posture across various data sources, AWS Security Data Lake has proven to be a game-changer for us
Why Amazon Security Lake?
Amazon Security Lake is an industry-leading and purpose-built data lake solution provided by Amazon Web Services (AWS), offering several distinct benefits that set it apart from other similar services.
- One of the most significant advantages of Amazon Security Lake is its scalability as Amazon Security Lake can easily accommodate the needs of organisations of any size. This scalability ensures that organisations can easily ingest, manage and analyse any amount of their security data without needing to be concerned about scaling issues or performance bottlenecks.
- In addition to its scalability, Amazon Security Lake also boasts exceptional integration capabilities with other AWS services, including Amazon S3, AWS Glue, and AWS Lambda and third-party sources and subscribers. This integration provides organisations with a comprehensive security analytics and data management solution, enabling them to extract valuable insights from their security data quickly.
- Amazon Security Lake’s flexibility in terms of data transformation and normalisation utilizing the OCSF format as stated earlier is another standout feature. It supports many data formats and sources, including log files, CloudTrail events, VPC Flow Logs, third party sources and more. This flexibility allows organisations to customise the solution to their specific needs and use cases, ensuring they can extract the insights they need to stay ahead of potential security threats.
- The solution offers pay-as-you-go pricing based on usage, with no upfront costs or long-term commitments. This pricing model makes it cost-effective and easy for organisations to budget and govern their security data management and analytics expenses.
- By providing encryption at rest and in transit, access control and audit logging to ensure the security of sensitive data – Amazon Security Lake gives organisations the peace of mind they need to protect their critical assets.