By Phil Massyn
One of the major challenges organisations are facing today is providing transparency into their current security posture which is able to provide both granular detail in addition to rolled up insights. Continuous assurance provides real time visibility into the performance against key metrics and KPIs which enables the federation of responsibility for security and compliance activities and full transparency across the business.
Continuous Assurance aims to answer the following questions:
- Is the risk level of my organisation within acceptable levels?
- Am I meeting my compliance objectives?
- Is my performance better this month than the month before?
- Will I pass my audit obligations?
- Which of my controls are not effective?
- What actions can I take to improve my security posture?
Why do I need Continuous Assurance?
We frequently encounter a common question from our clients: Why should I prioritise Continuous Assurance when I can simply utilise tool X to access my data?
Continuous Assurance isn’t meant to rival such tools; instead, its purpose is to offer a means of presenting their data at various organisational levels in a context that is meaningful for each. Although many security tools offer impressive built-in visualisations, they often lack customised perspectives for specific business units or the ability to merge data for a comprehensive compliance overview.
Apply a different lens
- Assuring Executive Board Confidence: Your Executive Board seeks assurance that the organisation’s security and compliance programs are effectively implemented.
- Enhancing Control Effectiveness: Your CISO aims to gain visibility into control domains that may not be operating effectively.
- Meeting Compliance Obligations: Your Compliance team requires assurance that the organization is meeting its obligations according to the Essential 8 (or any other compliance framework) standards.
- Empowering Departmental Heads: Departmental leaders want insights into how their teams can enhance the overall security posture.
- Enabling Technical Remediation: Technical teams desire visibility into a list of resources that fall short of security or compliance service level objectives, enabling effective remediation.
- Facilitating Auditor Insights: Your auditors intend to assess your organization’s security posture to identify any inherent risks that need to be reported to regulators.
- Leveraging Data for Informed Decisions: By leveraging data for security decisions, comprehensive views of business, risk, and control effectiveness can be generated from the same dataset.
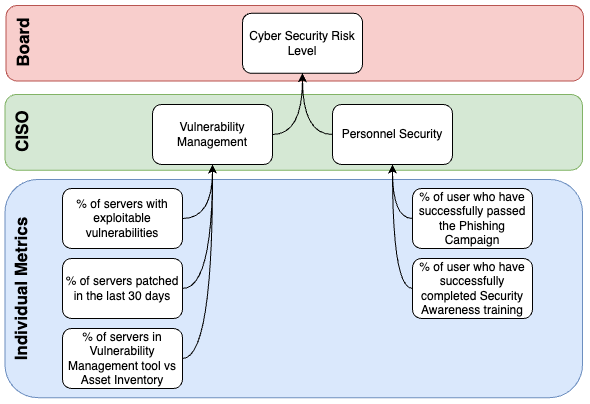
Rolling up the metrics
Metrics sourced from technical systems are extracted and parsed to provide a consolidated view. The true power of Continuous Assurance comes to fruition when you can systematically delve into the metrics, identifying the root causes behind unmet security and compliance objectives.
Technical Deep dive
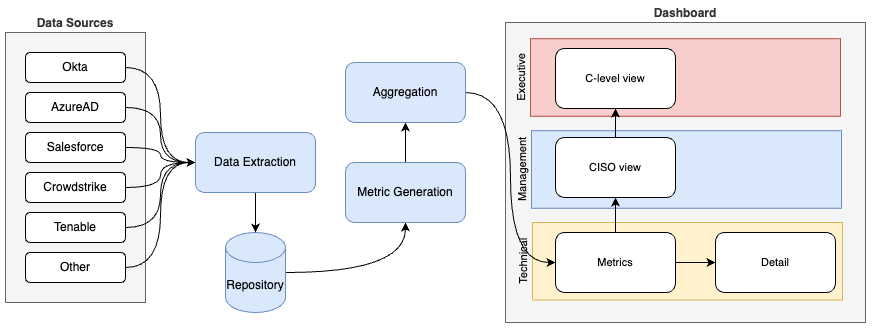
The Continuous Assurance platform initiates by extracting pertinent data from key sources, which is then stored within a data lake. Subsequently, metrics are generated and aggregated, aligning with industry compliance frameworks such as Essential 8, ISO 27001, and PCI DSS, to name a few.
At the core of the Continuous Assurance solution lies a reporting platform, often reporting platforms like Power BI or Tableau. This solution can seamlessly integrate with your existing infrastructure.
Diverse perspectives are crafted to align with customer specifications, risk profiles, industry frameworks, and standards. These customised views contribute to the ongoing assurance of security posture and controls.”
Let’s run through the process of creating your own Continuous Assurance platform.
What are you measuring?
Our process commences with a planning and brainstorming phase. Upon revisiting the core questions we aim to address, a range of metrics can be identified to provide insightful answers. Instead of attempting to formulate an exhaustive list of metrics, it’s advisable to begin with a modest selection and gradually expand your scope.
Presented below are initial metric suggestions to facilitate your starting point.
- Servers patched in the last 30 days
- Servers without exploitable vulnerabilities published less than 30 days ago
- Servers with a functioning anti-malware / EDR agent
- User accounts with MFA
- User accounts logged on in the last 30 days
- Websites running with valid SSL certificates
For simplicity, craft metrics as percentages, where a higher score signifies better performance.
Extracting the data
Having established a set of metrics, you can proceed to extract the required data. Most prominent security platforms offer modules dedicated to assisting with data extraction.
Develop code to effectively extract your data and store it within a suitable data storage solution, such as an AWS S3 bucket, Azure Storage Account, or a data lake.
Things to consider
- How frequently will the data extraction take place?
- What is the optimal duration for retaining this data?
- What data privacy factors should be considered when storing this data?
- What’s the procedure to initiate an alert or ticket in case of data extraction failure?
Generate the metrics
A critical element of your metric involves the data format. Defining a standardised data format that can be universally applied to all metrics is essential. A common format could entail a straightforward list of JSON objects.
[ { "resource" : "ServerName", "compliance" : 0, "detail" : "Server is running CentOS 7 was last patched on 2021-03-01" } ]
The JSON format proves highly effective, especially since it seamlessly integrates with serverless functions like AWS Lambda.
Adhere to this data format and ensure the file is saved using the metric name as the filename.
What if I don’t have the data?
Should the data be unavailable, it can serve as a catalyst for discussions regarding risk and security posture management. The absence of crucial tools and solutions might be amplifying risks within your organization.
Things to consider
- Data Retention Scope: What extent of data retention are you aiming for per metric? Daily or weekly snapshots?
- Additional Data Dimensions: Which supplementary dimensions should be incorporated into the data? Would mapping by business unit, runtime environment (cloud or on-premises) enhance insights?
- Choice of Programming Language: What programming language should be employed? SQL, Python, or another preference of your company’s comfort. Decisions should be guided by both delivery speed and maintenance convenience.
Aggregation
Within the data pipeline, a series of supplementary functions need to be executed. This entails identifying the metric, appending the metric column along with the datestamp to the dataset to allow for trending.
Once these fields are integrated, the data is ready for consumption by the reporting platform. As a component of the aggregation process, the system tallies both compliant and total resources. These figures play a crucial role in calculating the percentage, which is then cross-referenced with the datestamp and metric columns.
The outcome is a compacted table, primed for utilisation within the reporting tool.
Reporting
With metrics now consolidated into their respective percentages, you can initiate the creation of dashboards to address immediate inquiries.
Are the Company’s Security and Compliance Goals Attained?
Initiate by computing the average metric scores across all categories based on the datestamp. This approach generates a trend graph, enabling you to discern whether the scores are experiencing an upward or downward trajectory over time.
Which Metrics Demand Focus?
Apply a filter to the dataset based on the most recent data load and present a comprehensive list of metrics alongside their corresponding scores. This view serves to highlight the metric that exhibits the most substantial gap, influencing the overall score adversely.
Which Resources Require Remediation?
Delve into the data load files and identify the most recent load for each metric. Apply a filter based on compliance to provide your technical teams with a clear understanding of the items requiring remedial action.
Do it all again
Establishing a continuous assurance platform is a continual endeavor. After launching your initial dashboard, remain committed and enhance your metrics. As time progresses, additional metrics will be incorporated, while identifying and rectifying any issues within your existing metrics.
Enhancing the Platform: A Vision Forward
- Full Automation: Strive for complete automation across all processes.
- Introducing Comprehensive Dimensions: Extend the scope by incorporating additional dimensions such as business unit, environment, or geography to enrich insights.
- Implementing Service-Level Objectives (SLOs): Enhance metrics by introducing specific SLOs, allowing them to be categorised as “pass” or “fail” based on set benchmarks.
- Weighted Metrics: Differentiate the significance of metrics by assigning varying weights, acknowledging the varying importance of each.
- Diverse Perspectives: Explore the creation of distinct views catering to Compliance, Risk, and Business Objectives. Additionally, consider perspectives aligned with ISO27001, NIST, and Essential 8 standards.
- Enriched Resource Metadata: Augment the dataset by introducing enriched metadata to resources, encompassing elements like explanatory help text, supplementary URLs for deeper insights, and categorisation against security domains.
- Enhanced Categorization: Refine categorization through factors like the location of resources, their designated environment (Production, Development, Sandbox), and whether they are Internet-facing (true / false).
By embracing these strategies, we can propel the platform towards a more refined, comprehensive, and insightful solution, better suited to meet dynamic security and compliance demands.
Key Considerations to Keep in Mind
- Selective Data Extraction: Exercise caution while selecting data for extraction and measurement. Prioritise data privacy concerns, particularly when dealing with sensitive information.
- Data Retention Strategy: Determine the appropriate timeframe for data retention. For instance, if data is downloaded daily, decide whether to retain only one copy per day or perhaps one per month.
- Avoid Unjustified Exclusions: Refrain from making assumptions about exclusions. If a data source is incomplete, opt for reporting non-compliance rather than excluding the data. For example, if patching data is unavailable for cloud environments while available for internal systems, the metric should acknowledge the cloud systems but flag them as non-compliant due to missing patching data.
- Consistency with Policies: Metrics should consistently align with your established policies to maintain accuracy and credibility.
- Pragmatic Approach and Tolerance: Take a practical approach and allow for a certain degree of tolerance. Account for situations where short-lived instances (such as AWS EC2 Auto-scaling) could trigger false alerts. This might involve withholding reports on instances awaiting the application of key components or policies.
- Flexible Implementation of Policies: Factor in data synchronisation and operational realities. For example, if the password policy dictates changes every 90 days, consider reporting changes every 95 days to accommodate data synchronisation.
- Consideration for New User Accounts: Recognise that new user accounts might not have immediately changed their passwords. Reporting immediate non-compliance could be unnecessary within regular business processes.
- Credibility through Consistency: Maintain a consistent metric approach over time to foster user confidence in your reporting capabilities.
- Monitor Backend Processes: Create alert mechanisms to promptly detect and address failures in data extraction or metric generation, thereby ensuring the reliability of the system.
How can Mantel Group help?
Mantel Group possesses the necessary skills and expertise to guide you in establishing your Continuous Assurance platform. Our comprehensive support ranges from dedicated Cyber teams for compliance and governance to proficient Data Engineering and Infrastructure setup and management. Your chosen cloud platform, data pipeline, data lake, and preferred reporting engine can serve as the foundation for constructing your platform.
Get in touch with us today to explore the extensive capabilities Mantel Group has to offer for your Continuous Assurance needs.
Understand where the greatest opportunities lie to revolutionise your continuous assurance approach